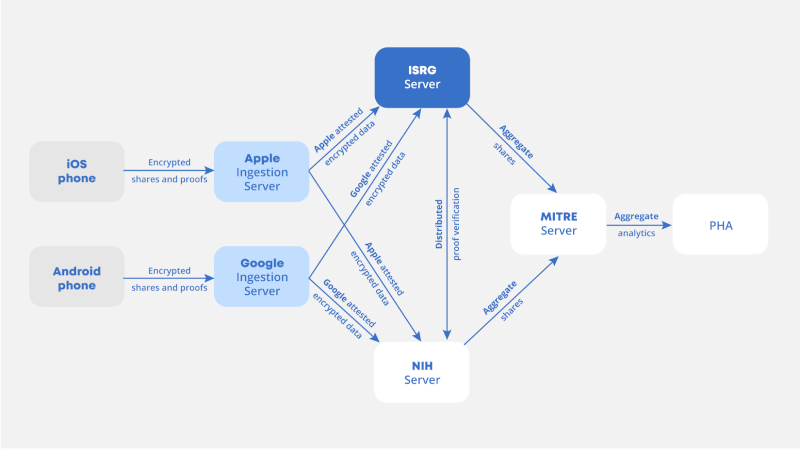
The Internet Security Research Group (ISRG) and the National Institute of Health (NIH) use MPC for extracting private analytics from COVID-19 Exposure Notifications from Google and Apple devices. The objective is to allow Public Health Authorities (PHAs) to collect meaningful data from user devices (e.g. the total number of exposure notification alerts) without exposing any one client’s data.
Mechanism
- Each user’s device data is split into two shares.
- Shares are encrypted on the user device with keys from the ISRG and NIH, respectively.
- Data shares are sent to ingestion servers operated by Google and Apple, who perform device authenticity verification and load balancing without learning anything from the shares.
- Data shares are passed to the ISRG and NIH, who combine them into a partial aggregate sum.
- The ISRG and NIH each send their partial aggregate sums to a server operated by MITRE. At this point, they are combined into a complete set of metrics that can be viewed by PHAs.
Code
GitHub - divviup/prio-server: A Prio server implementation.
Links
ISRG Prio Services for Preserving Privacy in COVID-19 EN Apps
Apple and Google Exposure Notification Privacy-preserving Analytics (ENPA) White Paper
Prio: Private, Robust, and Scalable Computation of Aggregate Statistics